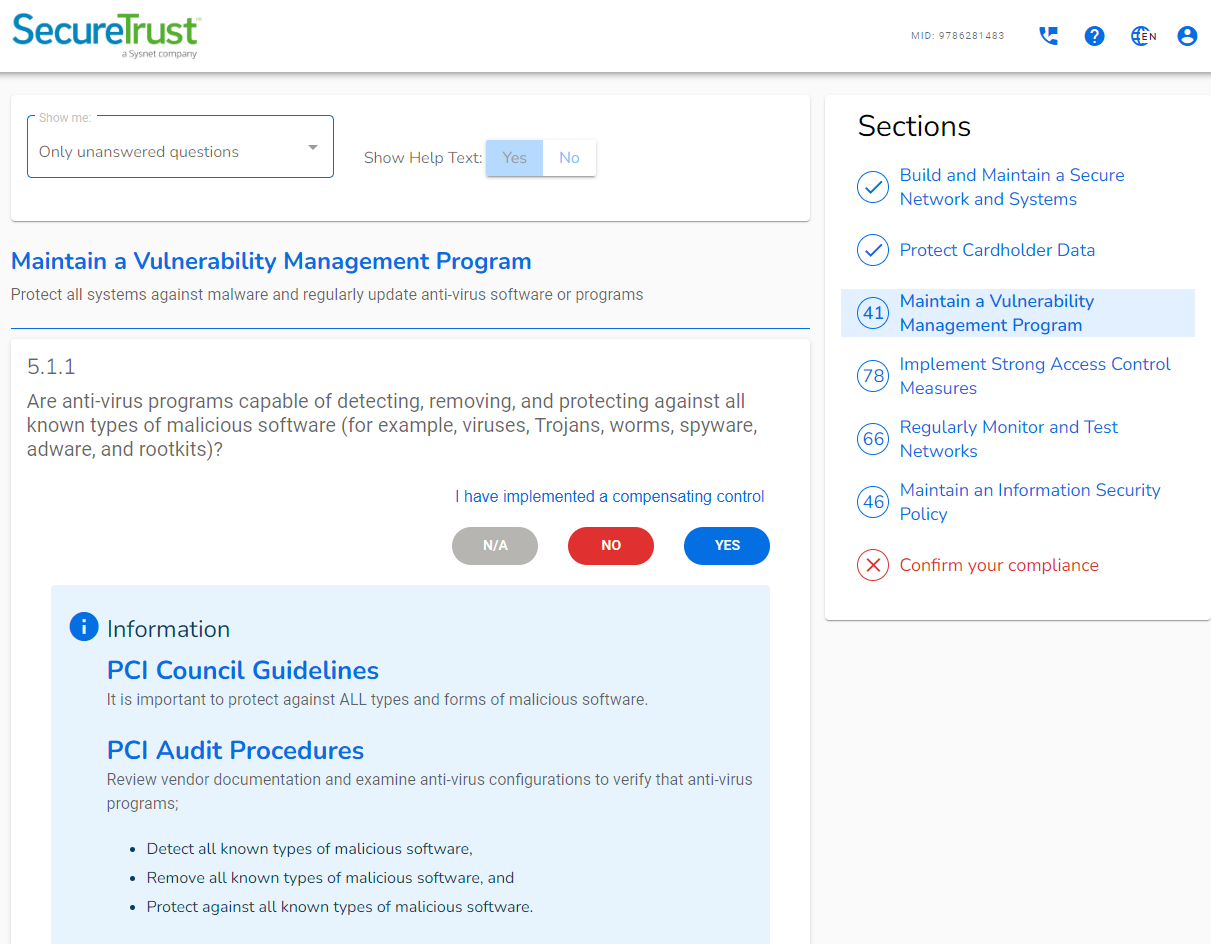
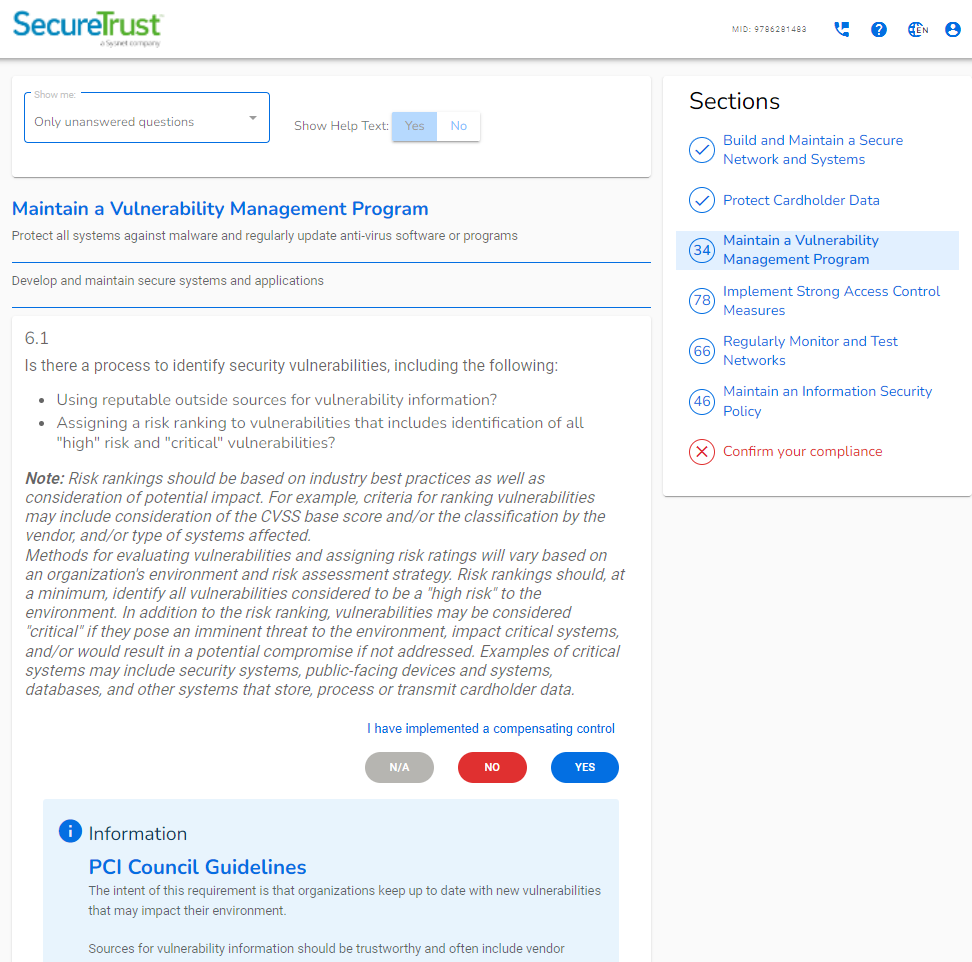
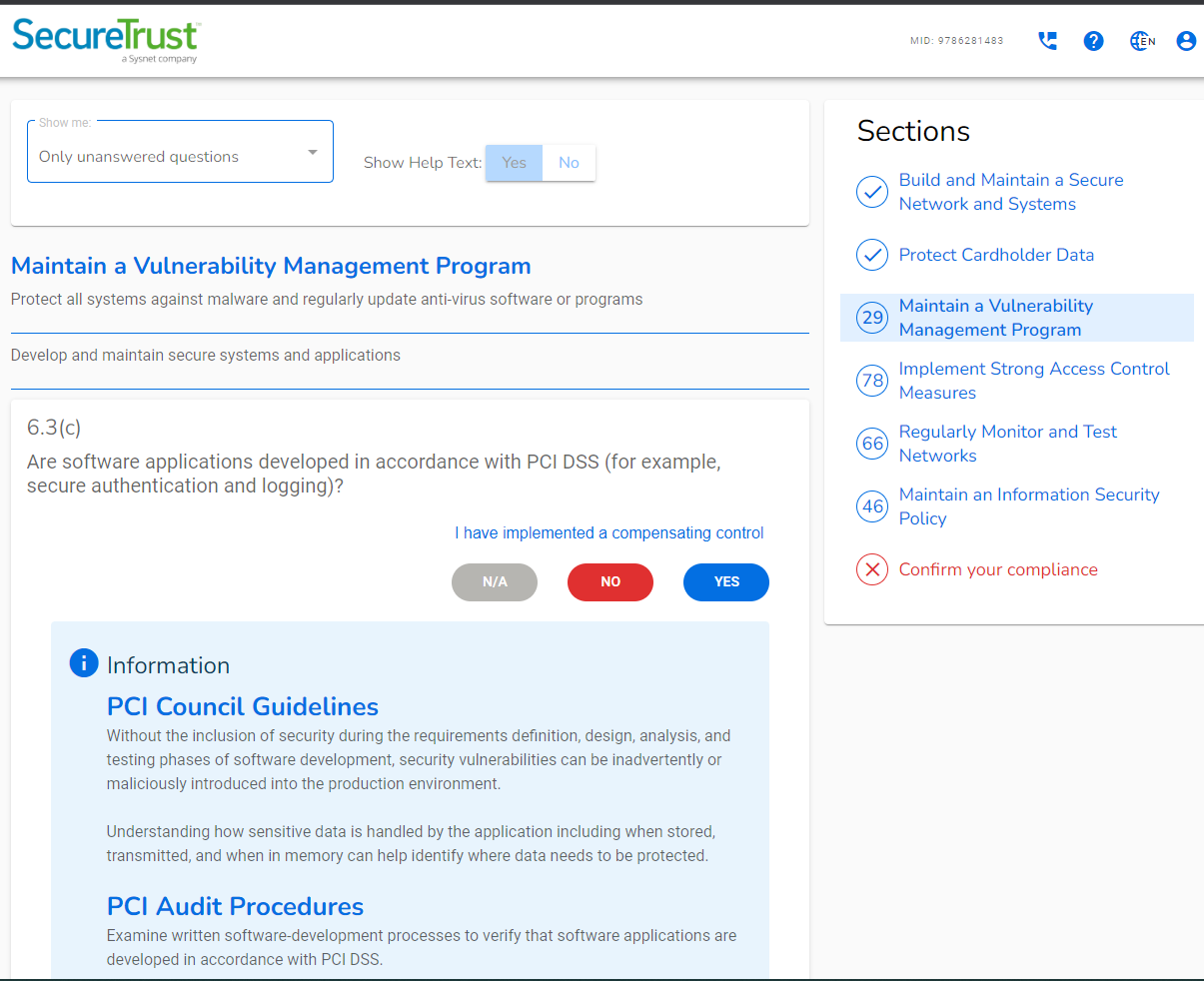
BlacTec's Red Team service consists of the following features:
Assigned Tactical Red Team Manager
Yearly threat modeling activity and assessment goal setting
Quarterly on-site debriefings and assessment goal realignment
Internet Reconnaissance reporting
Physical security assessment
Social Engineering testing throughout the year
Vulnerability assessment activities throughout the year
Ongoing network, application, wireless penetration testing
DELIVERABLES:
At the conclusion of each Red Team engagement, BlacTec Security will produce a findings and recommendations report containing:
An executive summary including;
The scope of the engagement
An overview of our activities
A high-level, categorical, risk-based breakdown of findings
High level recommendations
A high-level plan for remediation
Detailed findings
A risk-based list of addressable issues detailing the area of exploit, exploit description, risk to the environment, sophistication of the attack, impact of the finding, evidence and detailed remediation recommendations.
Detailed findings will be grouped as follows;
Social Engineering Findings
Physical security findings
Technology findings
Network (internal and external)
Application
Open Source Intelligence (OSINT) Findings
Response capability findings
In addition to the above report we will also produce;
A vulnerability DB including;
A list of vulnerabilities identified categorized out by host, CVE and criticality
A itemization of exposed services
A prioritized list of vulnerabilities requiring immediate attention
Detailed remediation guidance
A high-level project plan including;
Activities, cost rating, level of effort, benefits to the organization, complexity, sales impact if applicable and whether the project includes people, process or technology.
Identified Running and exposed services